Security
Training
Training
Training and awareness in software security is critical for the success of information security within the organization. Implementing a software security training program represents a challenge for information security managers. Key to a successful software security training is to teach the software development workforce in how to design and implement security controls and deliver web and mobile applications that are secure and resilient to attacks. IMQ Minded Security offers the following specialized Application Security Seminars and Trainings.
Instructor Led Training Courses
The following represents a schema of the security training courses that IMQ Minded Security delivers on-site to our customers:
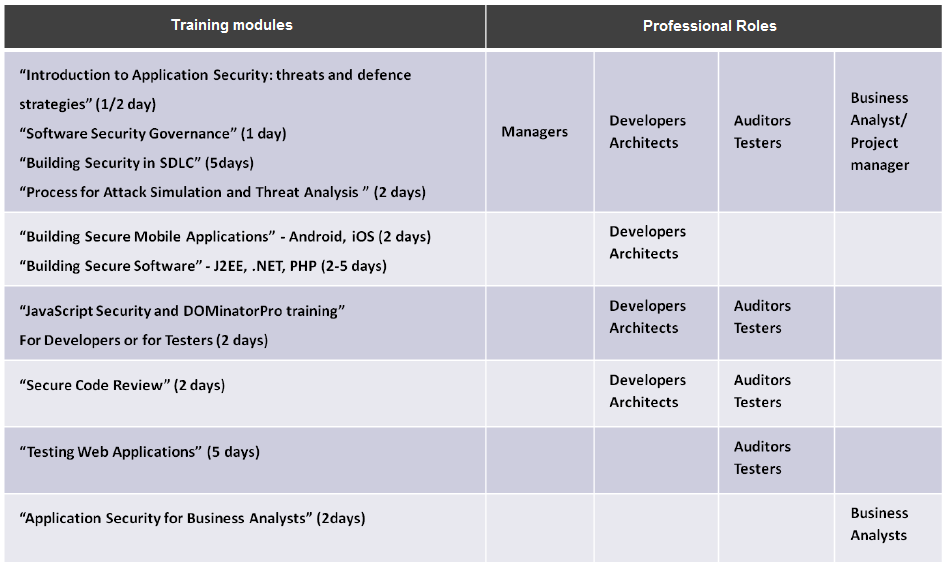
Introduction to Application Security
This is an introductory course with the main goal to create awareness for a wide audience of application stakeholders on security issues regarding online services. The course includes a demo of real attacks and different types of approaches to protect web applications from attacks. The course includes an assessment of the impact of vulnerabilities on corporate assets.
Software Security Governance
This course aims to provide a comprehensive overview of the processes to be carried out and possible solutions to improve your secure software development process.
Building Security in SDLC
This security training wants to provide tools for developing secure applications following a methodology for conducting a security analysis of the application without knowing the source code (black box assessment) and with knowledge of the source code (white box assessment). The course includes practical exercises and hands-on sessions on applications and sample source code. The training course includes four days of training and one day for the final exam.
Process for Attack Simulation and Threat Analysis
This course, which is useful for a wide audience, provides the ability to identify various risk factors of cyber-threats by following a structured process. The adoption of risk based threat modeling empowers information security risk managers in the identification of security measures that are effective in reducing the risk of cyber threats. This training will also give examples and use cases of architectural risk analysis and threat modeling and will help to identify countermeasures for the various types of cyber threats. It also helps software developers to apply the results of threat modeling to remediate issues in source code such and perform code level unit tests to test the e various functions.
Building Secure Mobile Applications (Android, iOS)
The objective of this security training course is provide software developers and architects with the tools and the methodologies that can be used to develop secure mobile applications avoiding the introduction of vulnerabilities in the source code. The training includes practical hands-on exercises on real type of mobile applications.
Building Secure Software (J2EE, .NET, PHP)
It aims to provide the tools and the methodology for developing Java, PHP or .NET code safely, avoiding the introduction of security issues. The course includes practical exercises and hands-on sessions on sample applications. The total duration of this security training course is five days. The first two days will focus on the approach for security testing web applications, the third and fourth days will focus on theory and practice of secure application development. The last day will be focused on a final exam.
JavaScript Security and Blue Closure Training
These courses objectives are to provide the tools and the methodology for testing or developing JavaScript code safely, avoiding the introduction of security issues in the source code. The courses include practical exercises and hands-on sessions on sample applications. The total duration of each course is two days.
Secure Code Review
This security training aims to provide the students with the tools and the methodology to perform a review of the security of the source code being developed. The course includes practical exercises and hands-on sessions on sample applications.
Testing Web Applications
It provides the tools and the methodology to conduct a security analysis of the application using the black box testing methodology which means without knowing the application source code. The course includes practical exercises and hands-on sessions on sample applications. This activity includes four days of training and a final day of examination.
Application Security for Business Analysts
This course aims to provide an approach to software security for business analysts. It will introduce the web application security as well as processes for secure software development, threat modeling and design of secure web applications and critical components.
Check our
Services Training.
A competitive non-stop 2 days secure coding challenge! The “IMQ Minded Security Hackathon Event” is designed to give developers a fun and challenging event that will create at the same time security awareness through a highly stimulative learning path. How it works Teams A set of developers teams register to the Hackathon competition. Tasks During […]
More infoLearn the methodology for developing JavaScript code safely, avoiding the introduction of security issues in the source code.
More infoLearn how to identify various risk factors of cyber-threats by following a structured process.
More infoWhat about training your developers to fix the vulnerabilities in your own code?
More info



