I would like to have more control of the outsourcer
If your company adopts an outsourcing software development model, Minded Security can support you to develop a Secure Software Assurance process with the aim to define all the criteria and all the steps necessary to guarantee an adequate assurance for the software you buy.
The model proposed to regulate the security features of the software that you want to purchase from a supplier involves the use of the following standards:
- OWASP Secure Software Development Contract Annex
- Capability Maturity Model v1.1
- ISO / IEC 27006: 2007 (Information technology – Security techniques – Requirements for bodies providing audit and certification of information security management systems)
The model aims to create a document shared between supplier and client in order to identify all the security features and a processes that allows to guarantee the level of assurance of the software wanted by the customer.The proposed process has 5 basic steps:
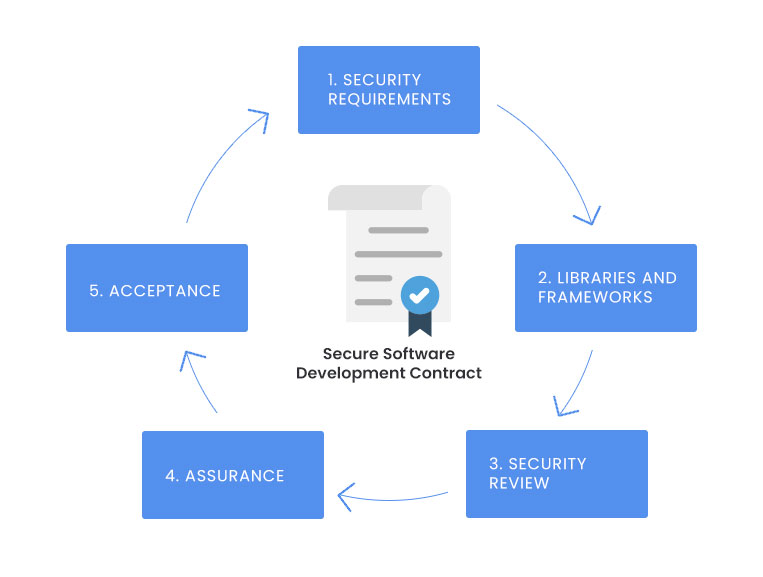
- Security Requirements: this area specifies the security features required by the required software
- Libraries and frameworks: The Supplier must indicate all third-party software used in the software (disclosure) and consider it as code provided by the supplier (evaluation).
- Security Review: this area specifies the right to review the code and to have access to the source code and access to test environments
- Assurance: the Certification Package is defined, the Self-certification of the supplier of the non-harmful code.
- Acceptance: In this phase the Certification & Accreditation (C&A) process is performed according to CMM v1.1